Authentication and Authorization : Which is which?
There has been a constant misconception about these two terms. In most cases, one has been used in place of the other. While others take both terms to mean the same thing. This write-up aims to break down these terminologies and eliminate these endless misconceptions.
What is Authentication?
Authentication is simply the process of proving or showing that something is true, right or genuine.
In Technology parlance, which is our focus, the above definition is not far from what this terminology connotes. Authentication is proving a User’s identity.
It deals with the question of who a User is. This is usually done by the user providing information shared between the user and the server. The Information may include the user id, username, password, pin code, fingerprints, iris recognition or biometrics.
On your iPhone, you want to access your application but your phone is locked. You are required to input your pin, pattern or fingerprint, these are modes of Authentication.
You are logging into your Gmail account through another device, there is a login prompt requiring you to input your username and password to access your account. These are forms of Authentication. I’ll explain the forms of Authentication extensively for more clarity.
Forms of Authentication
Password-Based Authentication
This is the common username and password login method. End-Users must provide the correct login credentials to access their account. The provided credentials are compared with the values previously provided and stored in the internal repository or otherwise the system.
For Developers, you know how common and important it is to have this form of authentication on your projects and applications.
To implement the Password-Based Authentication on your application, you can use Sessions, Cookies or Passport js when working with Node js
The Azure Active Directory Authentication by Microsoft is another amazing tool to implement the password-based form of authentication. The Azure AD includes other components that improve password security and reduces the need for desk assistance. They include Self-service reset, and hybrid integrations to improve password protection policies.
Biometric Authentication
This Authentication form is based on a user intrinsic factor, that is, something unique a user has that distinguishes it from other users. Fingerprints, voice and facial recognition are the major types of this authentication.
For Node Apps, there are a few reliable libraries and interfaces for implementing a biometric form of authentication. The ones I am familiar with are Web Authentication API and Own Id. You can check them out, they have robust documentation. The Azure AD Multi-factor auth supports this form of authentication.
Multi-Factor Authentication
This form of authentication requires a user to provide two or more credentials to verify the user’s identity. The sole aim is to add an extra layer of security to the authentication process. Two-factor authentication (2FA) is an example of this form of Authentication. The Authenticator App and Azure AD Multi-factor auth by Microsoft are one of the most popular tools for this authentication.
Certificate-Based Authentication (CBA)
The CBA uses a cryptography technique, a digital certificate to identify a user. The digital certificate is an electronic file that contains end-user information such as their name, email address and public key. The certificate is signed by a trusted agency, for instance, a web server. The certificate is checked against a list of certificates and the user is allowed access if the certificate is listed.
The most common CBAs are Transport Layer Security and Secure Sockets Layer.
Token-Based Authentication
A Token based authentication generates unique encrypted security tokens. The token provides users access to protected pages for a limited period without having to enter their login credentials each time they visit these pages
This form of authentication involves a six-step process; an access request is made when the user login, the server verifies the information entered by the user, and the server generates a secure encrypted token for the user which is transmitted to the user’s web browser who verifies the token, the user submits the transmitted token and is allowed access if the tokens match, the token remains active and would only expire if the user logs out or ends the session.
A common way of implementing this form of authentication is through the JSON Web Token (JWT). The JWT is an open internet standard that provides a detailed, contained way for transmitting information between parties(a client and server) as JSON objects.
Now here is the real deal, there is another term which has been associated with the JWT and the Authorization process - OAuth.
It can be argued that the misconception between the Authentication and Authorization terminologies as noted at the beginning of this article has been borne from the term OAuth. A lot of questions have been asked if OAuth is an Authentication or Authorization process.
Let’s look at the concept of Authorization to get a proper understanding of the OAuth.
What is Authorization?
We defined Authentication earlier as the process of proving something to be genuine, Authorization on the other hand is the process of granting permission to a resource. For context, while Authentication proves a user's identity, Authorization determines the user's permission rights. In other words, Authentication answers the question of who are you while Authorization answers the question of what are you allowed to do.
The Authorization process comes after the Authentication Process.
I have seen a lot of questions online on these concepts and several attempts have been made to give a clear answer to them, still, the confusions persist and rightly so because several libraries, web services and applications have chosen to use one term against the other. Some of these questions are:
Is OAuth an Authentication or Authorization process?
What is OAuth 2.0?
Is OAuth 2.0 Authentication or Authorization?
Do JWT and OAuth 2.0 mean the same thing?
What is OpenId 2.0 and is it the same as OAuth?
I will briefly try to throw light on these questions and give a proper understanding of these concepts.
Is OAuth an Authentication or Authorization process?
OAuth stands for "Open Authorization". It is an authorization protocol that grants third-party services easy and secure designated access. It allows third-party servers to exchange your information without password-based authentication.
Let us say you want users to log in to your website without the haggle of creating a password or entering a username, accounts of external services such as Google, LinkedIn, Github or Facebook can be used to access the website instead, that is OAuth (granting permission to an external resource/server).
Verdict: OAuth is an Authorization process.
What is OAuth 2.0?
OAuth 2.0 is an open-standard authorization protocol. It is a framework of the OAuth that provides specific authorization flows for web applications, server-side applications, browser-based applications, native/mobile apps and other devices. It replaced OAuth 1.0 in 2012 and is now the industry standard for online authorization. You can read the documentation for a detailed explanation.
Is OAuth 2.0 Authentication or Authorization?
From our verdict above, we can say OAuth means Open Authorization. However, there have been instances where OAuth has been used interchangeably with Authentication, hence the term Open Authentication which has got a lot of people including me in a wall of mazes confused.
The OAuth protocol that grants permission to a third-party or external resource involves Authentication as its first step. The Authorization flow is like a big mansion, that has a fleet of stairs inside the massive edifice. To get to the top and to get a proper view of the building and the amenities inside it, you would have to climb the stairs. The staircase in this context is the Authentication process and the entire building is the Authorization protocol.
There are libraries, services and applications that use OAuth, precisely OAuth 2.0 for its Authentication process alone.
Verdict: OAuth2.0 is an Authorization protocol but can be used as an Authentication tool
Do JWT and OAuth 2.0 mean the same thing?
This question has been asked vice-versa the differences between the two terms. Yes, the JWT and OAuth 2.0 do not, in any way mean the same thing.
While OAuth is an authorization protocol, JWT is only a token format.
As we concluded in the last verdict, OAuth 2.0 can be an Authentication tool. A lot of services use OAuth 2.0 as an Authentication tool alone, hence the term "social login".
How can OAuth 2 be used as an Authentication tool? Through Access Tokens. An Access Token or API Token is a piece of code with a large amount of data containing information about a user, permissions and timeframes that are passed from one server to another.
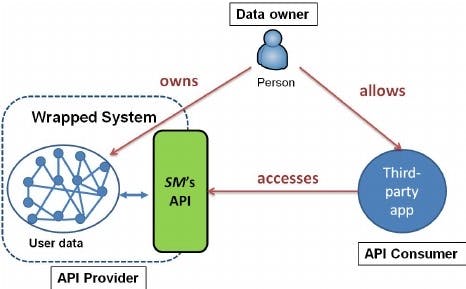
A Visual Representation of the OAuth Authentication Model by Vanilson Buregio
The OAuth 2.0 specifies how access tokens are transferred. There is where the server authenticates or identifies the resource owner before granting access. The OAuth 2 can use the JWT as a token specification.
Verdict: No, they do not mean the same thing. OAuth 2.0 is an authorization protocol that can use JWT as a token format.
What is OpenID 2.0 and is it the same as OAuth?
OpenID and OpenID 2.0 are open specifications for authentication and single sign-on. It is an old specification for authentication. It allowed users to use an existing account without needing to create new passwords. However, due to its low patronage and the use of OAuth 2.0 for authentication by libraries and other web services, the OpenID connect was created. OpenID Connect is a simple identity framework built on top of OAuth 2.0 by adding more values into OAuth 2.0 valid requests and responses to provide user identity information for authentication purposes.
Verdict: In other words, OpenID, OpenID 2.0 and OpenID connect are frameworks created for authentication purposes. Although OpenId connect was built on OAuth 2.0, it only provides authentication, not authorization.
Conclusion
I hope you were able to grasp the concept of Authentication and Authorization better than before and have a clearer understanding of both terminologies and other terms associated with them and the purpose of both protocols in the development domain.
If you have any questions, you can reach me on Twitter